Quantum Encryption Commercialization: 2025 Status & 2030s Outlook
Quantum encryption is no longer a lab curiosity. As quantum computing advances, organizations are moving from slide decks to real pilots and early rollouts. In practice, “quantum encryption” spans two tracks: (1) quantum key distribution (QKD), which uses the physics of photons to establish keys, and (2) post-quantum cryptography (PQC), which are new, classical algorithms designed to resist quantum attacks. The commercialization story in 2025 is the pragmatic blending of both: deploy PQC broadly where possible, apply QKD where risk profiles and fiber routes justify it, and build crypto agility so upgrades are repeatable rather than heroic one-offs.
What “Quantum Encryption” Really Means (Scope & Terms)
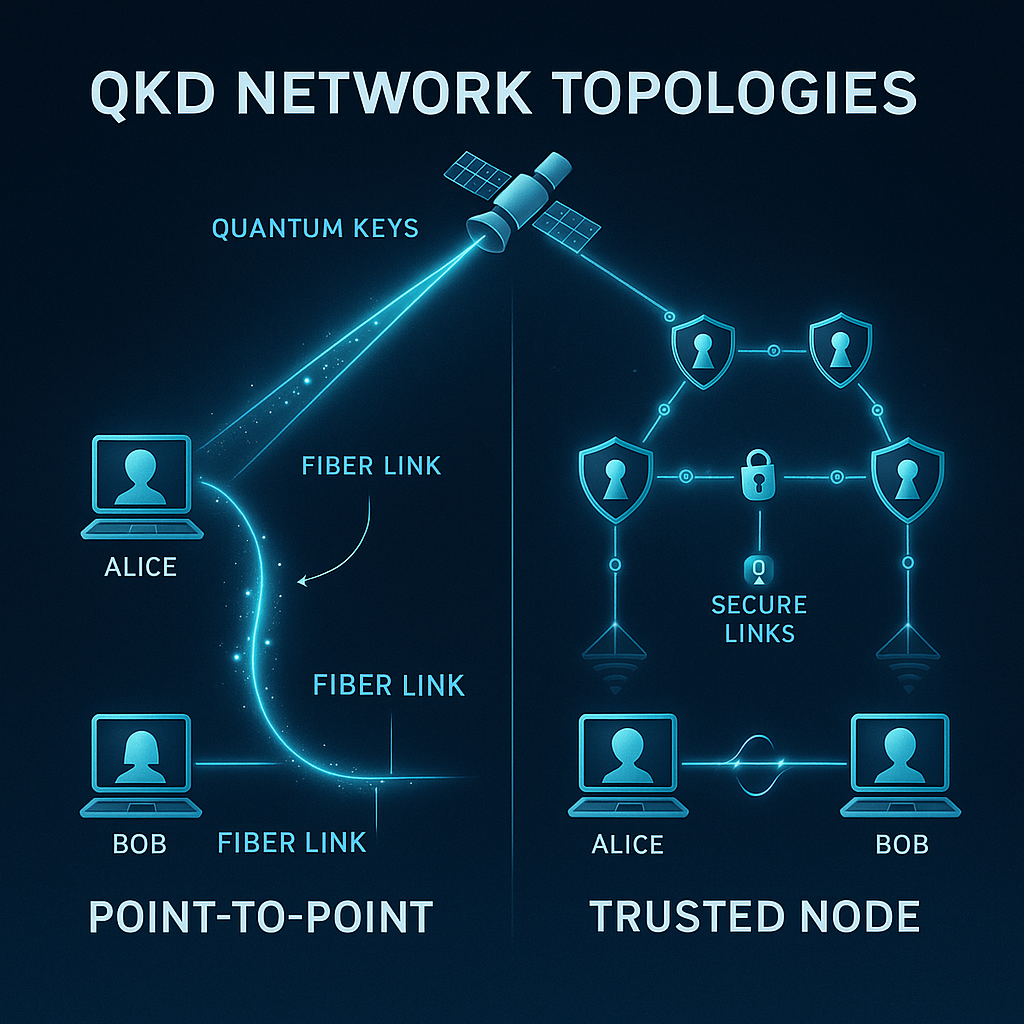
- QKD: Keys are encoded in quantum states so eavesdropping becomes detectable. It requires specialized optics and typically dark fiber or trusted nodes.
- PQC: New public-key algorithms (e.g., ML-KEM for key encapsulation and ML-DSA/SLH-DSA for signatures) standardized by NIST to withstand quantum adversaries using today’s networks and hardware. NIST finalized the first wave in 2024 (FIPS 203, 204, 205), a watershed moment for enterprise roadmaps.
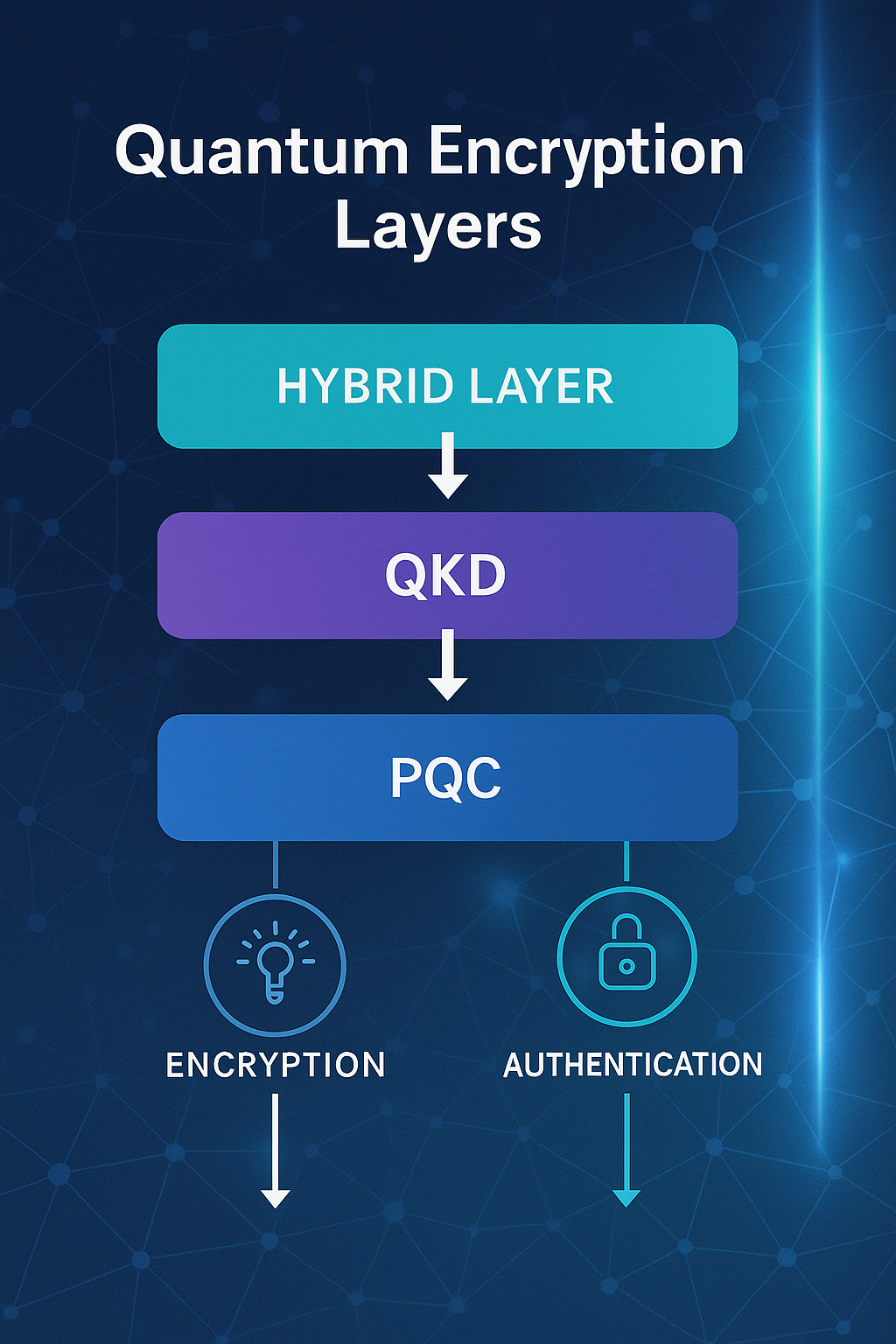
- Hybrid: Practical combinations—e.g., classical TLS plus a PQC key exchange—or injecting quantum-generated entropy into conventional key management, as seen in several vendor offerings.
Commercialization in 2025: Where We Actually Are
QKD deployments (selective but real)
- Mature vendors now ship 4th-gen QKD gear engineered for commercial networks (temperature-stable optics, smaller footprints, simpler ops). ID Quantique’s XG series is a representative example used in research, government, and financial backbones.
- Typical customers: national labs, defense, critical infrastructure operators, and Tier-1 carriers exploring metro-scale links. The economic sweet spot is high-value links over manageable distances with fiber control and low latency requirements.
PQC adoption (broadening quickly)
- Because PQC works over existing networks and CPUs, it’s moving faster than QKD. NIST’s 2024 standards give architects clear targets (ML-KEM/ML-DSA/SLH-DSA), unlocking vendor roadmaps and procurement policies.
- Major Internet and security platforms are piloting or enabling post-quantum options in TLS and origin connections; Cloudflare has documented these rollouts and guidance—“quantum-ready TLS” is shifting from demo to default.
Policy and readiness signals (accelerators)
- Governments and cyber agencies now publish concrete migration guidance. CISA’s PQC initiative and ENISA’s summaries help owners inventory crypto, plan upgrades, and avoid big-bang cutovers.
- The UK’s NCSC urges large organizations to prepare for migration by the early 2030s (identify critical services by 2028; complete transitions by 2035), underlining how long multi-year crypto projects can take.
Market Size and Growth: What the Numbers Say
- The quantum cryptography market (often QKD-led) was ~USD 518M in 2023 and is projected around USD 4.6B by 2030 (≈38% CAGR), per Grand View Research. Other firms place 2030 values in the mid- to high-single billions depending on scope and methodology.
- PQC-specific estimates generally show steeper curves given deployability via software/firmware and cloud stacks; multiple analysts project multi-billion by 2030 with 30–45% CAGR ranges.
Key Drivers You Can Bank On
- Harvest-now-decrypt-later: Adversaries can store today’s traffic and decrypt it in the future once quantum capabilities mature—making long-lived secrets urgent candidates for early PQC.
- Regulatory & procurement pressure: Once standards exist, policy follows—frameworks begin to require “quantum-safe” posture for critical systems and suppliers.
- Ecosystem readiness: Chipmakers, OS vendors, browsers, CDNs, and cloud providers are aligning behind standardized KEMs and signature suites, reducing integration friction.
Hard Problems That Still Matter
- QKD economics & reach: Link budget, fiber availability, and the lack of practical quantum repeaters limit scale; costs are falling but still significant versus software-only PQC.
- PQC performance & footprint: Some algorithms increase handshake sizes and CPU costs; embedded/IoT and high-throughput gateways may need tuning or re-architecture.
- Interoperability: Coordinating hybrid TLS, device PKI, and key management across vendors/geographies requires standards tracking and staged migrations.
- Organizational complexity: Crypto is everywhere—DBs, apps, HSMs, MDM, CI/CD, backups. Inventory and change control, not math, often become the bottleneck.
- Hype vs. delivery: Funding cycles can outrun maturity; focus on verifiable controls, not buzzwords.
A Pragmatic Enterprise Roadmap (12–36 Months)
1) Build a cryptographic inventory
Map where public-key algorithms and certificates live: TLS, VPN, code signing, firmware updates, MDM, messaging, backups, inter-service auth. Tag long-lived data flows and crown-jewel systems first.
2) Design for crypto agility
Abstract algorithm choices behind policy/versioning. Ensure stacks can rotate from RSA/ECC to ML-KEM/ML-DSA/SLH-DSA without breaking SLOs. Pilot hybrid KEMs on internal services, then customer-facing endpoints.
3) Pilot PQC where the blast radius is small
Start with internal APIs or regional endpoints. Measure handshake overhead, certificate sizes, and error rates. Tune caches, record sizes, and CDN behaviors accordingly.
4) Refresh PKI and key management
Update CA templates, HSM firmware, certificate profiles, OCSP/CRL tooling, and code-signing pipelines. Stage dual-stack (classical + PQC) hierarchies for transition periods.
5) Consider QKD for specific links
Where you control metro fiber between high-value sites (e.g., trading venues, DC-to-DC replication, gov/defense campuses) and the risk model justifies it, evaluate a QKD pilot—treat it as an adjunct, not a replacement for PQC.
6) Align with policy and partners
Follow CISA/NIST/NCSC timelines. Coordinate with cloud providers, CDNs, and top suppliers to keep configurations consistent across edge and origin.
Architecture Patterns That Work Now
- Hybrid TLS (classical + ML-KEM): Use PQC KEMs alongside classical ECDHE; if one breaks in the future, the session remains protected by the other. Watch handshake sizes/MTU to avoid fragmentation.
- PQC-ready PKI: Introduce ML-DSA or SLH-DSA for code signing and firmware once toolchains and secure-boot verifiers support them. Run parallel signing during cutover.
- Data-at-rest: Rotate envelope keys via KMS supporting PQC or ML-KEM wraps; record restoration procedures and crypto-era provenance in audit trails.
- QKD-assisted keying: In regulated, fiber-rich backbones, use QKD to seed/refresh symmetric keys on schedule; treat endpoints and key lifecycle controls as part of the trust boundary.
Regional Outlook (APAC lens, briefly)
- China continues to invest in QKD networks and satellite-assisted experiments.
- Japan and South Korea emphasize PQC migration strategies with telecom pilots.
- Expect accelerated public-sector demand and cross-border standards alignment as global supply chains adopt PQC-capable stacks.
KPIs to Track During Migration
- Coverage: % of external services and internal APIs speaking hybrid/PQC.
- Performance: Handshake latency, failure rates, CPU/throughput deltas vs classical baselines.
- PKI readiness: # of subordinate CAs and code-signing flows upgraded.
- Third-party alignment: % of top suppliers with PQC roadmaps and SLAs.
- Risk reduction: % of long-lived secrets now protected under PQC or QKD-assisted keying.
What to Watch Next
- Standard hardening: Profiles for IoT/OT; guidance for constrained devices and time-sensitive networking.
- Toolchain maturity: Audited libraries, HSM support, FIPS validations.
- Vendor consolidation: Quantum hardware + security software + telecom integrations.
- Policy deadlines: Sector rules that turn “nice to have” into mandates across finance, health, energy, and government.
Conclusion — From Hype to Habits
The commercialization of quantum encryption is no longer theoretical: PQC is standardizing and deploying at Internet scale, while QKD is carving out high-assurance niches. The organizations that win the 2030s will make quantum safety a habit, not a hero project—inventory cryptography, design for agility, pilot early, and align with standards and partners. By doing so, you will defuse harvest-now-decrypt-later risk and avoid a messy, last-minute scramble when quantum capabilities cross the practicality threshold.
Sources
- NIST — PQC Standardization (FIPS 203/204/205, 2024)
- Cloudflare Blog — State of PQC on the Internet (2023–2024)
- CISA — Quantum-Readiness Guidance (2023–2025);
ENISA — PQC Overview;
NCSC — Migration Advice - ID Quantique — QKD Commercialization (XG Series)
- Grand View Research — Quantum Cryptography Market Outlook;
MarketsandMarkets — Forecasts to 2030